
2 the weapon of choice
Overlap data to create all-source fusion
Entity, Link and Property:Analyst questions drive the Data Model
Delivering actionable intelligence for key challenges today



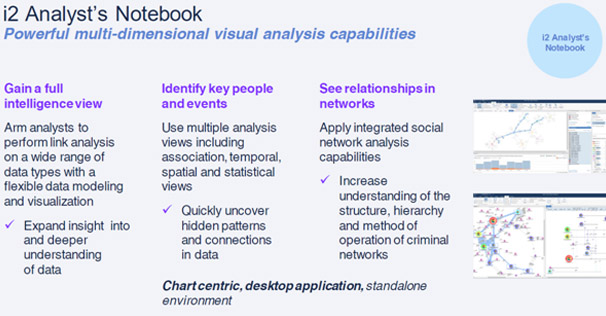
The i2 Products:



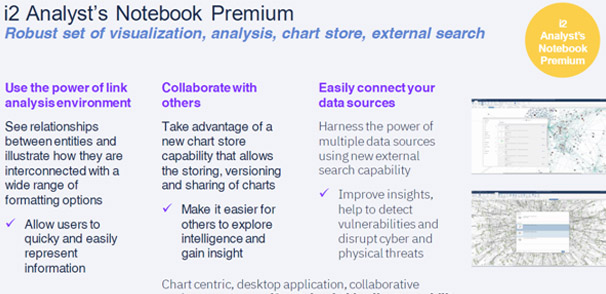
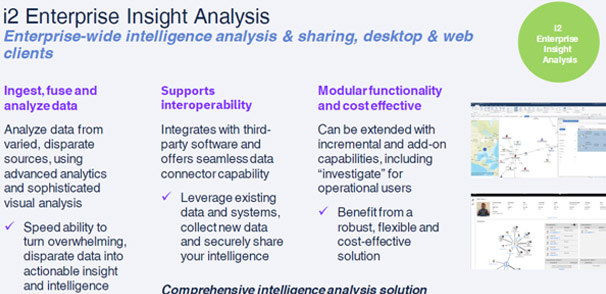
© All Rights Reserved
All product names, logos, and brands are property of their respective owners. All company, product and service names in this website are for identification purposes only.
